Setting Up a Free OpenVPN Server in Google Cloud Platform(GCP)
Setting Up a Free OpenVPN Server in Google Cloud Platform(GCP) in Less Than 5 Minutes
The VPN we are going to mention here:
- Is free: GCP provides e2-micro instance type for free on US region and we will be utilizing this along with free disk space and egress traffic
- Can be used for both internal and external traffic: Whether you want to connect to other GCP services or compute instances internally or route all of you computer’s traffic over the VPN, this way can be used
- Is limited to two active connections: In this specific post, we will walk through by using OpenVPN from marketplace which has limitation of 2 parallel users under free tier. In next post, we are going to show how this can be expanded
- Configurable through admin console: We can configure user account, vpn & network configuration, download ovpn file through web UI of OpenVPN
- Is very straight forward to setup: With just few clicks and without going through terminal, we can get our VPN server ready!
If we can setup a free VPN server in less than 5 minutes, why make it a long story? :) Let’s dive in directly
Create static IP address
We don’t want to loose IP address of the VPN which will be a real pain. So, reserve a static IP address in the region of your choice. This can be done through 2 ways:
- Using CLI:
gcloud compute addresses create $ADDRESS_NAME --region=$REGION - Through GCP Console: Go to reserve a static address page and reserve a regional IPV4 address.
Launch VPN Server
- On GCP Marketplace page, search for “openvpn access server” and select the one, then hit the LAUNCH button
- Here, we select e2-micro instance type which has 2vCPU and 1 GB memory.
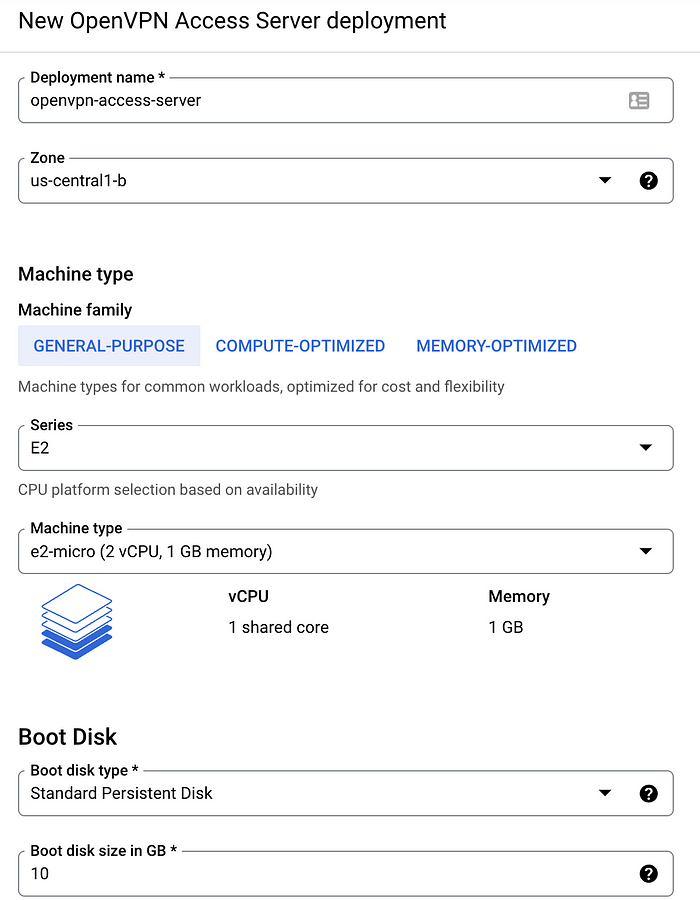
3. On the “Networking” section, choose the IP address that was reserved earlier with variable ADDRESS_NAME and hit “DEPLOY”
Within a few minutes, you will see the OpenVPN server is created and in the “Deployment properties” column in the right, it give us the admin URL, admin user and password for login like below.
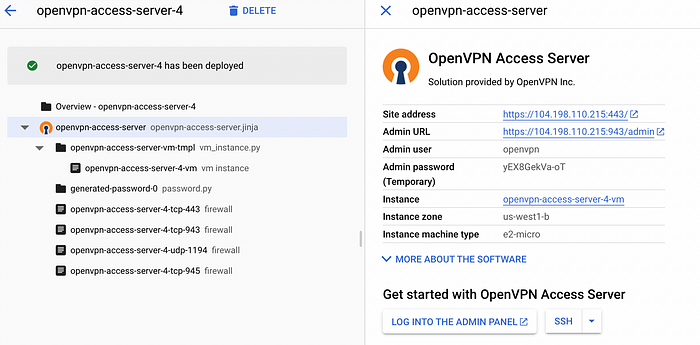
Now, we can login to the “Site address” using the credentials to get config “ovpn file” with all the connection strings, certificate etc.
After logging in, we can see links to download OpenVPN installer files as well as the “ovpn file” at the bottom under “ Yourself (user-locked profile)” link.
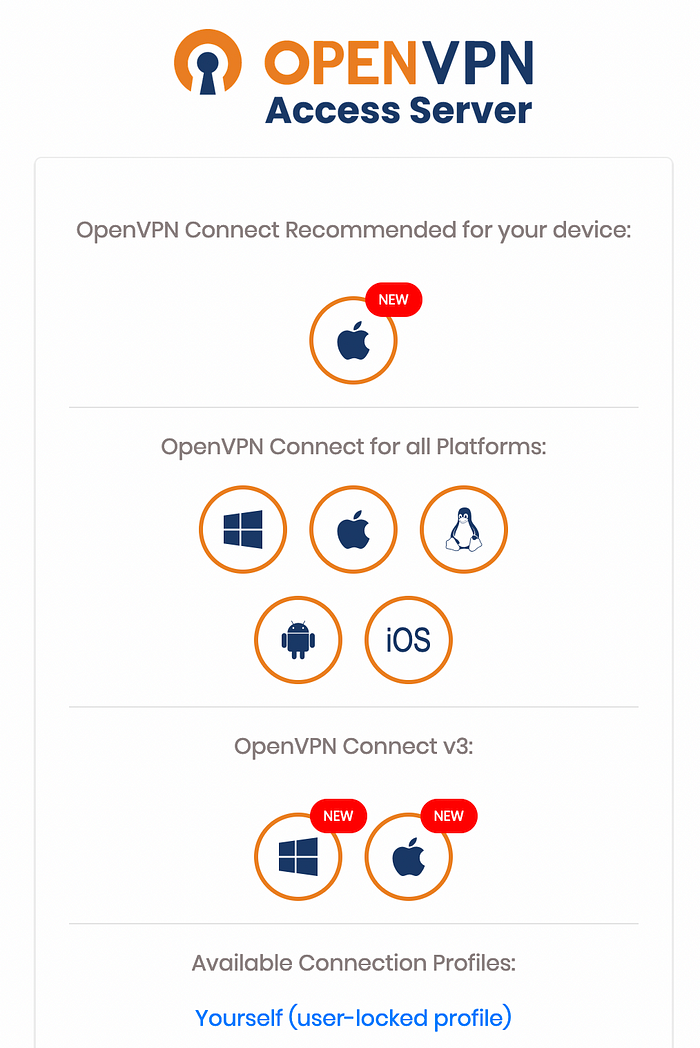
Now, we can use OpenVPN Connect or any of vpn applications to connect the vpn by using ovpn file. On the OpenVPN Connect, we can directly import the ovpn file which was downloaded from earlier step after logging in to the UI console.
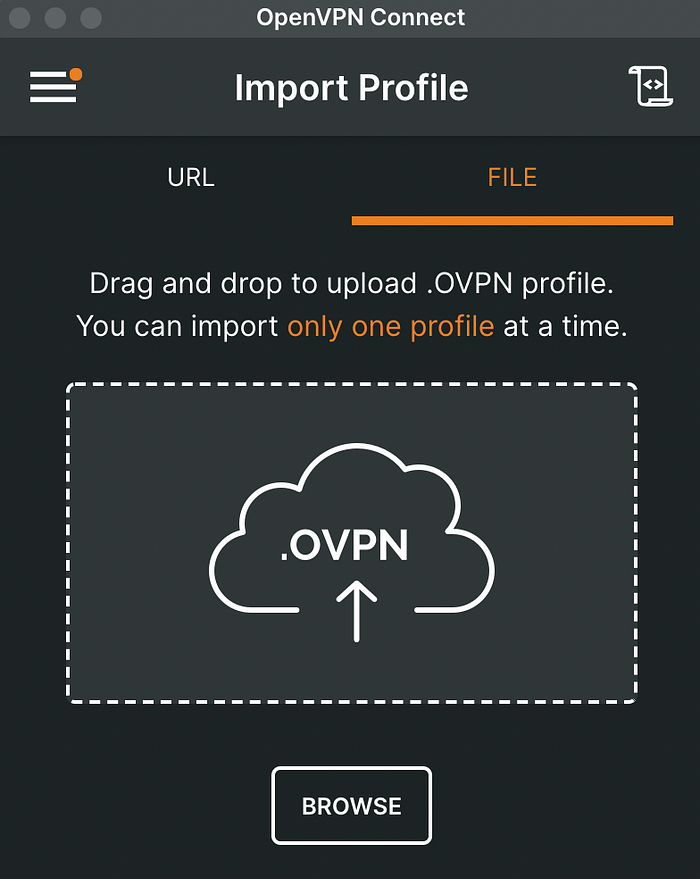
Once the profile is imported, we can connect to the VPN using the password shown on “Deployment Properties” from the marketplace deployment. Make sure to save a copy of the password.
Let’s confirm if the VPN is working or not!
We can see traffic in/out on the CONNECTION STATS also
 |
Alternatively, we can confirm by reaching out another compute instance within the same network using internal IP address.
For testing, we can simply ping the internal IP of the VPN instance itself.
YAY! Now, we have our VPN ready! It doesn’t cost a single buck.
Here, we saw on how to access GCP’s internal resource through the vpn but our normal traffic is not flowing through the VPN. If you just curl or load icanhazip.com or any of IP address finder, you will see your ISP provided IP address.
Let’s route all of our traffic from the VPN with these steps:
- Go to OpenVPN admin console and login with the URL https://[IP]/admin or the admin URL is shown on the Deployment Properties also. On the first login, we have to accept Terms and Conditions.
- Head over to “VPN Settings” and on the “Routing” section, mark “Should client Internet traffic be routed through the VPN?” to “Yes”
- On “DNS Settings” field, turn “Have clients use specific DNS servers” to “Yes” and enter a DNS server IP like: 8.8.8.8, 1.1.1.1 which are of Google and Cloudflare respectively.
- Save the changes with a restart
Now, if you check your IP address or browse http://icanhazip.com/, then it will show your VPN instance’s IP address means all your traffic is routed through the newly created OpenVPN server.
Comments
Post a Comment